Is that really your CEO emailing you?

What is an email impersonation attack?
Email impersonation attacks are a type of phishing attack where the attacker impersonates a legitimate sender (often a CEO or other high-level executive within the company) in order to trick the recipient into clicking on a malicious link or attachment.
These attacks are typically used to steal sensitive information such as login credentials or financial information. In some cases, attackers may also use email impersonation to deliver malware to the victim’s system.
Email impersonation attacks can be difficult to detect, as the attacker will often use a fake email address that is similar to the legitimate sender’s address.
If you are unsure whether an email is legitimate, you can always contact the supposed sender directly to verify its authenticity. Remember, never click on any links or attachments in an email unless you are certain that they are safe. To ensure you don’t get caught out in the future, we recommend setting up Microsoft’s “External email warning message”.
Setting up Microsoft’s “External email warning message”
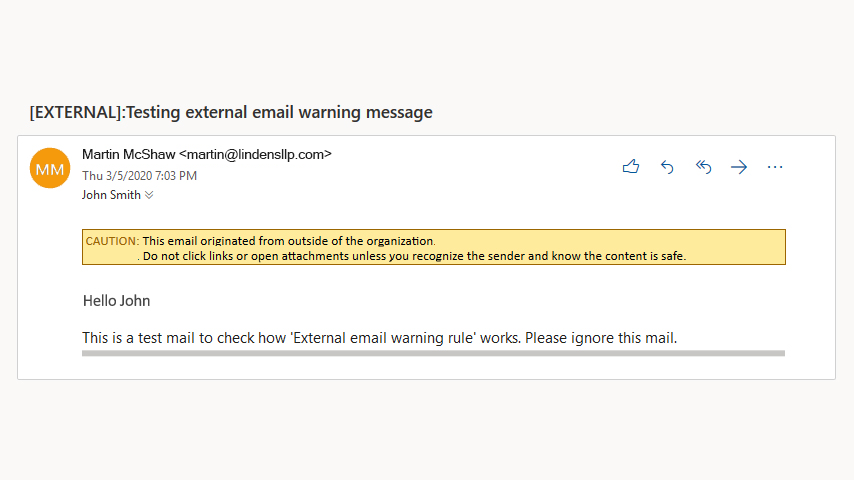
Office 365 by default has implemented an anti-phishing policy that uses automated mechanisms to recognise phishing emails and move them to the Junk folder in the email box.
You can extend this feature by adding an automatic warning message for all external emails.
Any email that comes to one of your email addresses from outside the company would have a message at the top similar to the one above. So, although it may look like it came from an employee inside the company, you can see straight away that it hasn’t.
You can apply this message for all users in the company, or only specific users. There is no additional license cost, as the system is built into Microsoft’s 365 email platform. If you need help with the process, speak to your IT team, or external IT provider.
Next steps
If you would like to find out more about staying safe from cyber attacks, please get in touch to talk about our range of cyber security solutions and how they can help your business.
We offer a 3-step approach:

If you’re unsure where to start and would like to have an informal chat about cyber security, please get in touch.
Useful links
National Cyber Security Centre (NCSC)
NCSC Exercise in a box
Metropolitan Police Cyber Protect
Sort-IT Cyber Security Solutions
