In today's digital age, ensuring the security of your Windows PC is paramount. That’s a given! With the constant threat of malware, viruses, and cyber-attacks, it's natural to want to beef up your defences. However,...
Read More
Cyber Security News
Is that really your CEO emailing you?
What is an email impersonation attack? Email impersonation attacks are a type of phishing attack where the attacker impersonates a legitimate sender (often a CEO or other high-level executive within the company) in order to...
Read More
A fake WiFi hotspot and a £5 voucher: gateway to an all-you-can eat data buffet
The target 100+ group of business owners and employees attending a conference for a national services group franchise, at a central London hotel. We’re keeping any specific details anonymous for the purpose of this article....
Read More
Prevention is better than cure: protecting your small business against cyber threats
The majority of small business’s cyber crime starts with human error, with just over half of cyber attacks being the result of employees clicking on links in phishing emails. This can open the door to...
Read More
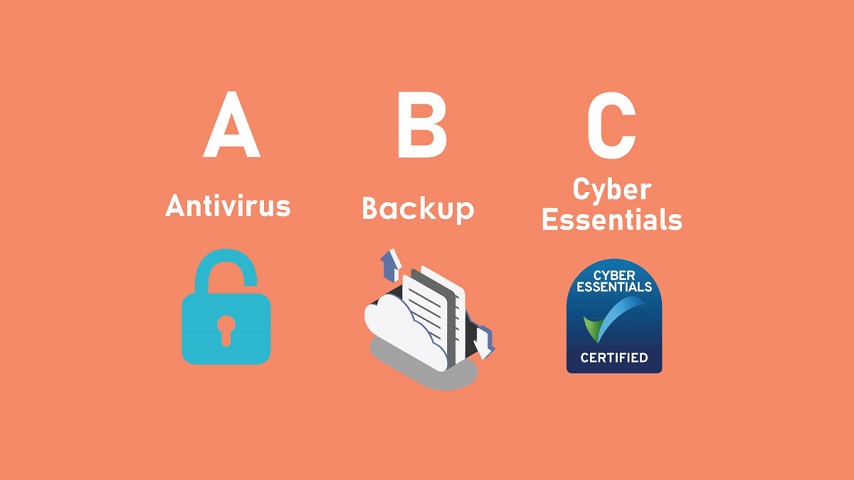
Our ABC of Cyber Security
Could you be a target for a cyber criminal? YES! Everyone's a target! With hybrid working becoming the norm, many of us are accessing our company IT systems and data from numerous locations and devices;...
Read More
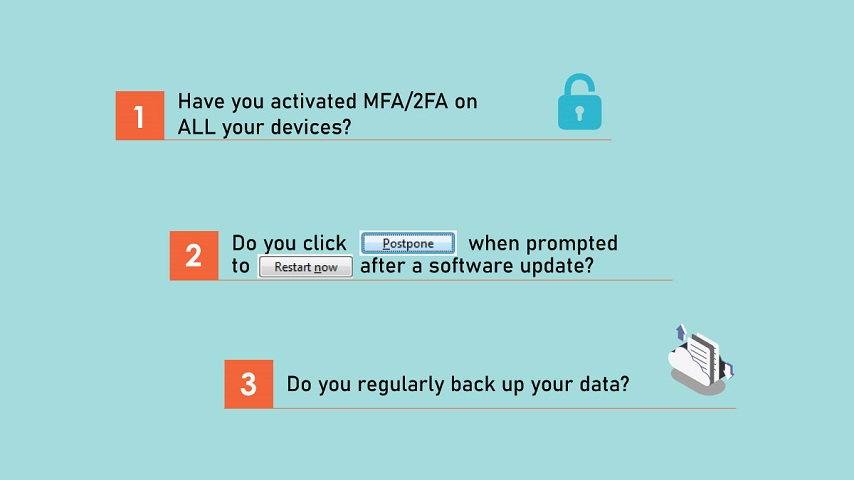
Three quick questions about your cyber security habits
How secure is your data from a cyber attack? With hybrid working becoming the norm, many of us are accessing our company IT systems and data from numerous locations and devices; maybe even using our...
Read More
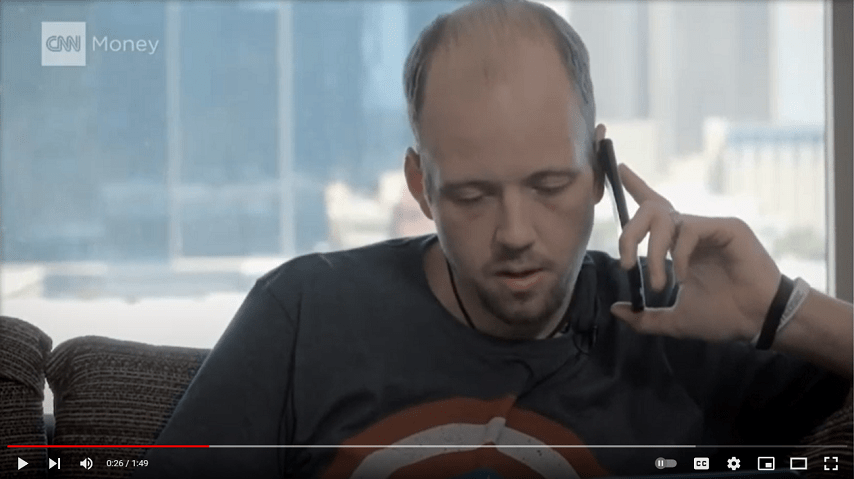
A 2-minute phone call and a fake link – watch how a hacker operates
The video below shows just how easy it is for cyber criminals to gain access to an employee's computer, giving them full access to the company's internal network. And once in, hackers can cause all...
Read More